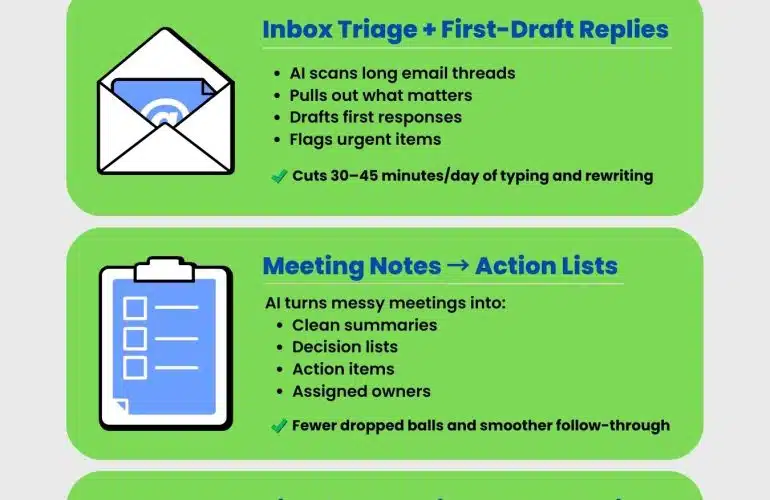
The Hidden Bottleneck Killing Your Q1 Productivity (It’s Not Your People)
If you're a business owner, you've had this exact thought: "Why does everything take longer than it should?" Not because your people are bad. Not because they don't care. But…

 480-464-0202
480-464-0202